728x90
반응형
최근 이메일을 통해 포르노 영상을 다운로드할 수 있다고 유도하여 클릭시 악성코드를 다운로드 받게 하는 악의적인 스팸 메일이 유포되는 것을 확인하였습니다.
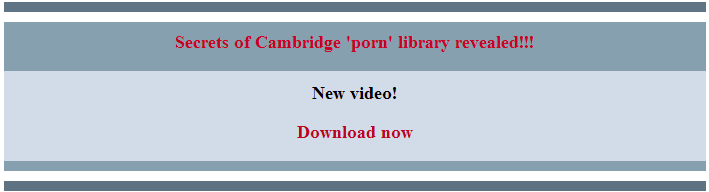
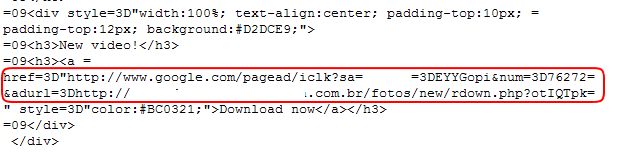
다운로드되는 파일 정보는 다음과 같습니다.
news_m.exe
- Size : 1433 Bytes
- MD5 : 189EB501DAE14FCFCD3CCA1D3AD607F3
- Packer : FSG
<진단 상태>
Antivirus Version Last Update Result
AhnLab-V3 2008.2.16.10 2008.02.15 -
AntiVir 7.6.0.67 2008.02.15 TR/Downloader.Gen
Authentium 4.93.8 2008.02.15 Possibly a new variant of W32/new-malware!Maximus
Avast 4.7.1098.0 2008.02.15 -
AVG 7.5.0.516 2008.02.15 Downloader.Small.60.BF
BitDefender 7.2 2008.02.16 Generic.Malware.dld!!.E155904C
CAT-QuickHeal None 2008.02.16 (Suspicious) - DNAScan
ClamAV 0.92.1 2008.02.15 -
DrWeb 4.44.0.09170 2008.02.16 Trojan.DownLoader.origin
eSafe 7.0.15.0 2008.02.14 suspicious Trojan/Worm
eTrust-Vet 31.3.5541 2008.02.15 -
Ewido 4.0 2008.02.15 -
FileAdvisor 1 2008.02.16 -
Fortinet 3.14.0.0 2008.02.16 -
F-Prot 4.4.2.54 2008.02.15 W32/Downloader-Sml-based!Maximus
F-Secure 6.70.13260.0 2008.02.15 Suspicious:W32/Malware!Gemini
Ikarus T3.1.1.20 2008.02.16 Trojan-Downloader.Win32.Harnig.bl
Kaspersky 7.0.0.125 2008.02.16 Heur.Downloader
McAfee 5231 2008.02.15 -
Microsoft 1.3204 2008.02.16 TrojanDownloader:Win32/Small.gen!Z
NOD32v2 2880 2008.02.15 a variant of Win32/TrojanDownloader.Tiny.NDF
Norman 5.80.02 2008.02.15 Suspicious_F.gen
Panda 9.0.0.4 2008.02.15 Suspicious file
Prevx1 V2 2008.02.16 -
Rising 20.31.30.00 2008.02.14 -
Sophos 4.26.0 2008.02.16 Troj/Sload-Gen
Sunbelt 2.2.907.0 2008.02.14 VIPRE.Suspicious
Symantec 10 2008.02.16 Downloader
TheHacker 6.2.9.221 2008.02.15 -
VBA32 3.12.6.1 2008.02.14 -
VirusBuster 4.3.26:9 2008.02.15 Trojan.DL.Nanodesu.Gen
Webwasher-Gateway 6.6.2 2008.02.15 Trojan.Downloader.Gen
Additional information
File size: 1433 bytes
MD5: 189eb501dae14fcfcd3cca1d3ad607f3
SHA1: 2fc782cfa4e188de34180670673674871d4a7fdf
- Size : 1433 Bytes
- MD5 : 189EB501DAE14FCFCD3CCA1D3AD607F3
- Packer : FSG
<진단 상태>
Antivirus Version Last Update Result
AhnLab-V3 2008.2.16.10 2008.02.15 -
AntiVir 7.6.0.67 2008.02.15 TR/Downloader.Gen
Authentium 4.93.8 2008.02.15 Possibly a new variant of W32/new-malware!Maximus
Avast 4.7.1098.0 2008.02.15 -
AVG 7.5.0.516 2008.02.15 Downloader.Small.60.BF
BitDefender 7.2 2008.02.16 Generic.Malware.dld!!.E155904C
CAT-QuickHeal None 2008.02.16 (Suspicious) - DNAScan
ClamAV 0.92.1 2008.02.15 -
DrWeb 4.44.0.09170 2008.02.16 Trojan.DownLoader.origin
eSafe 7.0.15.0 2008.02.14 suspicious Trojan/Worm
eTrust-Vet 31.3.5541 2008.02.15 -
Ewido 4.0 2008.02.15 -
FileAdvisor 1 2008.02.16 -
Fortinet 3.14.0.0 2008.02.16 -
F-Prot 4.4.2.54 2008.02.15 W32/Downloader-Sml-based!Maximus
F-Secure 6.70.13260.0 2008.02.15 Suspicious:W32/Malware!Gemini
Ikarus T3.1.1.20 2008.02.16 Trojan-Downloader.Win32.Harnig.bl
Kaspersky 7.0.0.125 2008.02.16 Heur.Downloader
McAfee 5231 2008.02.15 -
Microsoft 1.3204 2008.02.16 TrojanDownloader:Win32/Small.gen!Z
NOD32v2 2880 2008.02.15 a variant of Win32/TrojanDownloader.Tiny.NDF
Norman 5.80.02 2008.02.15 Suspicious_F.gen
Panda 9.0.0.4 2008.02.15 Suspicious file
Prevx1 V2 2008.02.16 -
Rising 20.31.30.00 2008.02.14 -
Sophos 4.26.0 2008.02.16 Troj/Sload-Gen
Sunbelt 2.2.907.0 2008.02.14 VIPRE.Suspicious
Symantec 10 2008.02.16 Downloader
TheHacker 6.2.9.221 2008.02.15 -
VBA32 3.12.6.1 2008.02.14 -
VirusBuster 4.3.26:9 2008.02.15 Trojan.DL.Nanodesu.Gen
Webwasher-Gateway 6.6.2 2008.02.15 Trojan.Downloader.Gen
Additional information
File size: 1433 bytes
MD5: 189eb501dae14fcfcd3cca1d3ad607f3
SHA1: 2fc782cfa4e188de34180670673674871d4a7fdf
해당 샘플은 다운로더 기능을 하는 파일로 다음과 같은 파일을 추가적으로 인터넷 임시폴더(C:\Documents and Settings\사용자계정\Local Settings\Temporary Internet Files)에 다운로드 합니다.
http://pousxxxxxcantonatureza.com.br/xxxxx/new/loca.exe (163,840 Bytes)
- MD5 : 78729D8F489358A3A8003142EBC1E811
- Trojan.Win32.Agent.epo
http://pousxxxxxcantonatureza.com.br/xxxxx/new/vshost.exe (93,184 Bytes)
- MD5 : 8FF9619D48BBF751C22712C418174567
- Trojan.Win32.Agent.exq
- MD5 : 78729D8F489358A3A8003142EBC1E811
- Trojan.Win32.Agent.epo
http://pousxxxxxcantonatureza.com.br/xxxxx/new/vshost.exe (93,184 Bytes)
- MD5 : 8FF9619D48BBF751C22712C418174567
- Trojan.Win32.Agent.exq
해당 다운로드된 파일은 시스템 폴더에 다음과 같은 것들을 설치합니다.
C:\Windows\System32\_it.bat
C:\Windows\System32\CcEvtSvc.exe -> Trojan.Win32.Agent.exq
C:\Windows\System32\drivers\Ols47.sys -> TROJ_ROOTKIT.EZ
C:\Windows\System32\etipogfr.tmp
C:\Windows\System32\CcEvtSvc.exe -> Trojan.Win32.Agent.exq
C:\Windows\System32\drivers\Ols47.sys -> TROJ_ROOTKIT.EZ
C:\Windows\System32\etipogfr.tmp
생성되는 프로세서 정보
C:\Windows\System32CcEvtSvc.exe -> 새로운 서비스 항목 추가
loca.exe
vshost.exe
loca.exe
vshost.exe
레지스트리 Key 생성 정보
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\SafeBoot\Minimal\System Reserved
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\SafeBoot\Network\System Reserved
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Enum\Root\LEGACY_CCEVTSVC
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Enum\Root\LEGACY_CCEVTSVC\0000
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Enum\Root\LEGACY_CCEVTSVC\0000\Control
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Enum\Root\LEGACY_OLS47
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Enum\Root\LEGACY_OLS47\0000
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Enum\Root\LEGACY_OLS47\0000\Control
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\CcEvtSvc
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\CcEvtSvc\Security
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\CcEvtSvc\Enum
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet002\Control\SafeBoot\Minimal\System Reserved
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet002\Control\SafeBoot\Network\System Reserved
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\System Reserved
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Network\System Reserved
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_CCEVTSVC
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_CCEVTSVC\0000
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_CCEVTSVC\0000\Control
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_OLS47
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_OLS47\0000
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_OLS47\0000\Control
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\CcEvtSvc
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\CcEvtSvc\Security
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\CcEvtSvc\Enum
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Ols47
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet002\Services\Ols47
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\SafeBoot\Network\System Reserved
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Enum\Root\LEGACY_CCEVTSVC
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Enum\Root\LEGACY_CCEVTSVC\0000
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Enum\Root\LEGACY_CCEVTSVC\0000\Control
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Enum\Root\LEGACY_OLS47
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Enum\Root\LEGACY_OLS47\0000
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Enum\Root\LEGACY_OLS47\0000\Control
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\CcEvtSvc
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\CcEvtSvc\Security
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\CcEvtSvc\Enum
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet002\Control\SafeBoot\Minimal\System Reserved
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet002\Control\SafeBoot\Network\System Reserved
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\System Reserved
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Network\System Reserved
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_CCEVTSVC
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_CCEVTSVC\0000
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_CCEVTSVC\0000\Control
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_OLS47
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_OLS47\0000
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_OLS47\0000\Control
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\CcEvtSvc
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\CcEvtSvc\Security
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\CcEvtSvc\Enum
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Ols47
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet002\Services\Ols47
레지스트리 value 삭제 정보
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\CrashControl]
MinidumpDir = "%SystemRoot%\Minidump"
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet002\Control\CrashControl]
MinidumpDir = "%SystemRoot%\Minidump"
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\CrashControl]
MinidumpDir = "%SystemRoot%\Minidump"
MinidumpDir = "%SystemRoot%\Minidump"
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet002\Control\CrashControl]
MinidumpDir = "%SystemRoot%\Minidump"
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\CrashControl]
MinidumpDir = "%SystemRoot%\Minidump"
레지스트리 value 수정 정보
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\ServiceCurrent]
(Default) = 0x0000000B
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\ServiceCurrent]
(Default) = 0x0000000B
(Default) = 0x0000000B
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\ServiceCurrent]
(Default) = 0x0000000B
하나의 악성코드를 통해 추가적으로 다른 악성코드를 다운로드하는 방식의 샘플이었습니다.
* 해당 분석은 보안 관련 비전문가의 분석(분석 사이트 활용을 통한 분석)이므로 오류가 있을 수 있습니다.
728x90
반응형